Vishing impersonates a reputable source, such as a credit card company, internet provider, or government agency, to get personally identifiable information (PII) fraudulently using speech technology. Vishing is carried out by attackers using VoIP software and mobile devices to make phone calls. To seem more legitimate, victorious individuals may employ phony phone numbers, artificial intelligence (AI), social engineering, smishing (text/SMS attacks), and voice-altering software.
Attackers conceal their actual voice and any regional accent they may have by using voice-altering software. It is more difficult to identify whether a number or call is fraudulent because several valid 2FA techniques use automated calls to generate one-time pins (OTPs).
Why is vishing a growing cyber threat?
It is simpler to persuade victims that vishing calls are from a reliable source and are of use to sophisticated technologies like voice-altering and caller ID spoofing. Voice-altering software can mimic or eliminate a caller’s accent, and caller ID spoofing can make fraudulent numbers appear legitimate.
AI technology has made it possible for robocalls to sound more lifelike. It is becoming increasingly challenging to discern between legitimate communications and vishing attempts because of the proliferation of deepfake technology on the market. Even worse, anyone can use the majority of these technologies for free.
How does a vishing attack work?
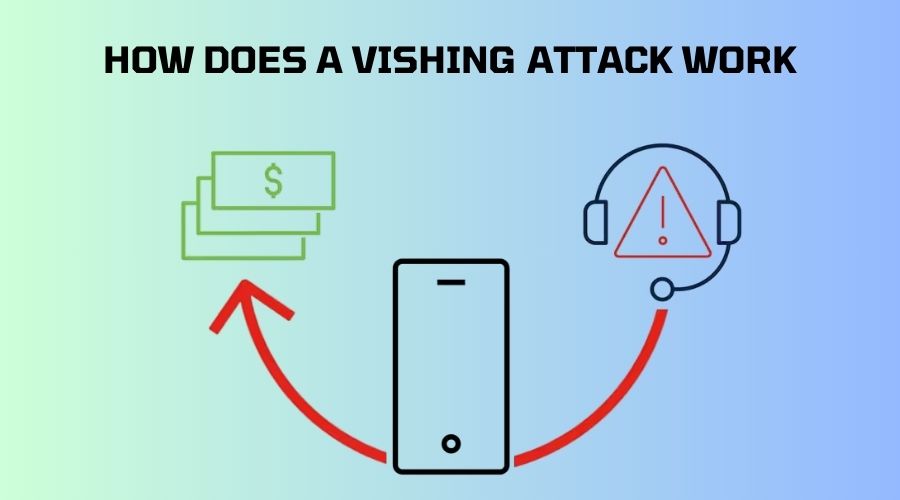
Target identification
This stage may seem like a targeted attack by cybercriminals, but it is more of a blitz. Vishers use autodialers to make hundreds of calls to known numbers in the hopes that a potential victim will answer and the line will be live. Data breaches, data brokers, personal search websites, and specific techniques such as parsing social media websites and web browsers are some of the ways they get phone numbers.
Although they don’t actively seek out people, Vishers might target particular age groups. Due to their susceptibility to urgency-based messages and potential lack of awareness regarding potential fraud, the elderly are a prime target.
Impersonation
Vishers utilize government organizations like the IRS or services you use daily to support their claims. Caller ID spoofing can make the scammer appear more reliable and remove the dubious nature of an unknown number.
To get a quick response, voicemails frequently use formal language with a hint of urgency. Cutting-edge AI deepfake technology can translate across languages and conceal accents with ease. These technologies increase the attacker’s chances of capturing a victim and further lessen the possibility of raising red flags.
Psychological manipulation
Psychological manipulation is a common tactic used by Vishers to keep you on the line after these investigators have you. Most Vishers have no problem utilizing guilt or threats to attempt to get your private information if the tactful method doesn’t work.
Sayings like “you received the service and need to pay for it” are examples of guilt, which is more of an attack on your character. Threats are more frightening or consequence-based and typically focus on legal action, such as an arrest, a lawsuit, or jail time if you don’t cooperate.
Data theft and exploitation
The attacker’s ultimate objective is to steal your sensitive data, which is never a good thing if all of the Vishers’ methods are successful. Once the attacker has access to your account or personal data, they can use it to commit financial fraud, identity theft, open new credit lines, and more.
On the dark web, Vishers are also known to sell data to data brokers, various people, search engines, and other criminals. In essence, your data is a gift with limitless potential, and if you don’t take precautions to secure your identity, they know how to take full advantage of it.
Technologies used in vishing attacks
Vishing attack technologies make it simple for attackers to obtain information from unwary targets.
- Voice over IP (VOIP) spoofing
- AI-generated voices (deepfake)
- Interactive Voice Response (IVR)
Types of vishing attacks
Vishing assaults differ depending on the target of the attack. The majority of attackers can profit more by selling personal information to people-search websites or data brokers; not all visitors are trying to steal your identity or money. There are numerous ways for a visitor to take your information, regardless of what they do with it.
Banking and financial fraud
- Fake bank call scams
- Loan and investment scams
- Credit offer scams
Tech support scams
- Fake Microsoft or Apple support calls
- Remote access scams
Government and tax agency impersonation
- IRS and other tax authority scams
- Medicare and Social Security scams
Corporate and business vishing attacks
- CEO fraud (Whaling)
- HR and payroll scams
How to protect yourself from vishing attacks?

- Calls from unknown numbers should be ignored: Do not answer a voicemail from a number you are not familiar with if you are unable to identify the caller. For privacy reasons, legitimate businesses typically leave voicemails with very little information.
- Automated holds should be avoided: It’s probably a scam if you answer the phone and are put on hold right away with a generic “please hold” message. When a real company calls you, they don’t immediately put you on hold.
- Check the identity of the caller: Tell them you will call them back using the official number from their website or account portal if they say they are from a company you do business with.
- If the caller is pressuring or threatening you, end the call. Threats of legal action, account termination, or demands for immediate payment are examples of aggressive strategies used by vishers to get a prompt response. No respectable business will put you under this kind of strain.
- Use number blocking and spam call filters. Fraud warnings and spam filters are provided by numerous cellphone operators. By turning these features on, you can steer clear of shady calls.
- Don’t give out private information on the phone. Businesses won’t call and request personal information, passwords, or OTPs. It is a warning sign if someone asks for this information.
- Have faith in your intuition. Instead of taking the chance, it is safer to end the call and inquire directly with the business if something seems strange.
Monitor Your Accounts
Please delete data from non-essential fields or submit a removal request to remove any non-essential personal information from the compromised account. After that, keep an eye out for any unusual activity on the account.
It can take a lot of time to complete data removal requests and conduct routine account monitoring. You might want to think about using a go-between, such as the data erasure tool offered by ExpressVPN. It gives fraud alert efforts, files all necessary data removal requests, and keeps an eye out for any unusual activity on the account. And for more safety tips from cybercrime, visit www.megafeedz.com.
FAQs
Q1. What distinguishes phishing from vishing?
Ans: Vishing is a counter to phishing that uses voice-based techniques rather than the email-based attacks that phishers employ. The objective of both attacks is the same, regardless of how the techniques differ: to gather as much information as possible.
Q2. AI vishing: what is it?
Ans: Artificial Intelligence (AI) vishing uses cutting-edge technology to alter an attacker’s gender, mimic or eliminate accents, or even translate scripts into a different language. Because artificial intelligence (AI)-generated voices increasingly sound less robotic than those produced by earlier software, it is more difficult to tell if a caller’s voice is artificial intelligence (AI).
Q3. Can vishing occur on social media, Telegram, or WhatsApp?
Ans: Any software that enables voice calling, such as WhatsApp, Telegram, and social media platforms like Facebook Messenger, can be used for vishing. The good news is that using these services will increase your protection against vishing because the majority of popular messaging applications employ end-to-end encryption (E2E) to conceal text and voice messages sent and received between devices.